QUESTION 69
The following list gives examples of records that may be evidence of how an organisation has fulfilled the requirements of clause 8.4 of ISO 9001. Match the records to the appropriate requirement of clause 8.4.
Explanation:

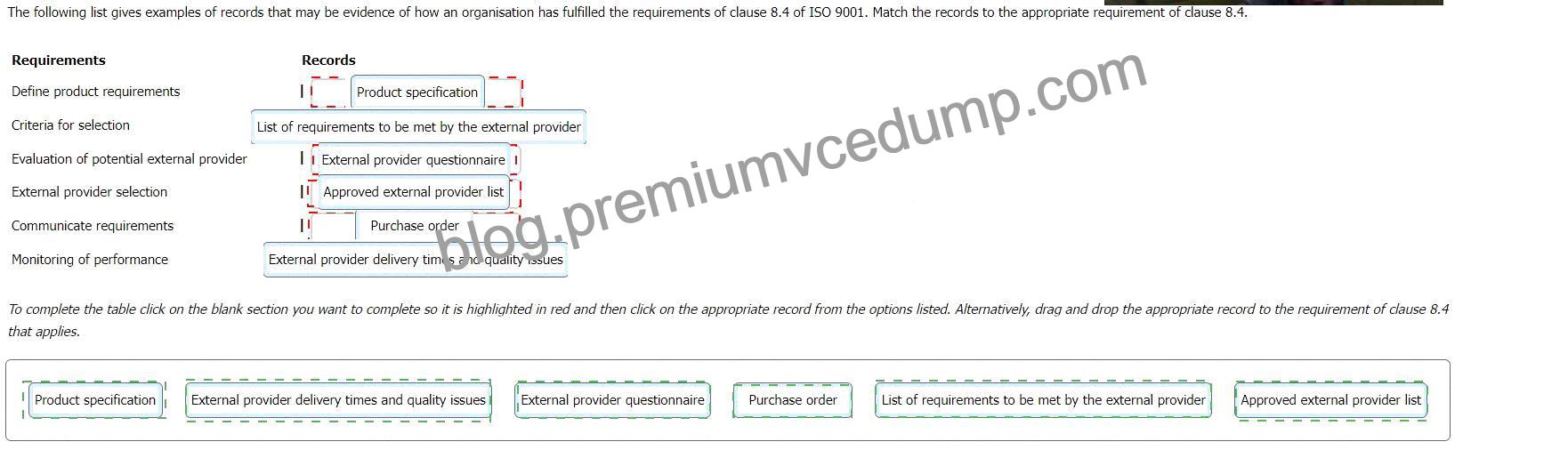
The following table shows the possible matching of the records to the requirements of clause 8.4:
Table
Requirements
Records
Define product requirements
Product specification
Criteria for selection
List of requirements to be met by the external provider
Evaluation of potential external provider
External provider questionnaire
External provider selection
Approved external provider list
Communicate requirements
Purchase order
Monitoring of performance
External provider delivery times and quality issues
Comprehensive and Detailed Explanation: = According to clause 8.4 of ISO 9001:2015, the organization should ensure that externally provided processes, products, and services conform to the specified requirements. To do so, the organization should:
Define the product requirements that are relevant for the external provision, such as specifications, drawings, standards, codes, etc. These should be documented and communicated to the external provider. A record of the product specification can be used as evidence of this requirement.
Establish the criteria for the selection, evaluation, and re-evaluation of external providers, based on their ability to provide processes, products, and services in accordance with the requirements. The criteria should be documented and applied consistently. A record of the list of requirements to be met by the external provider can be used as evidence of this requirement.
Evaluate the potential external providers before selecting them, using the established criteria. The evaluation methods may include questionnaires, audits, references, samples, etc. The results of the evaluation should be documented and reviewed. A record of the external provider questionnaire can be used as evidence of this requirement.
Select the external providers that have demonstrated their competence and conformity to the requirements.
The selection should be based on the evaluation results and the organization’s needs. The selection should be documented and approved. A record of the approved external provider list can be used as evidence of this requirement.
Communicate the requirements for the processes, products, and services to be provided by the external provider, including the verification and validation activities, the acceptance criteria, the documentation requirements, the changes control, etc. The communication methods may include purchase orders, contracts, agreements, etc. The communication should be clear, complete, and timely. A record of the purchase order can be used as evidence of this requirement.
Monitor the performance and conformity of the external provider, using the established criteria and methods.
The monitoring methods may include inspections, tests, audits, feedback, complaints, etc. The monitoring results should be documented and analyzed. A record of the external provider delivery times and quality issues can be used as evidence of this requirement.
References: ISO 9001:2015, [ISO 9001 Auditing Practices Group Guidance on Scope], Mastering the Scope of ISO 9001 Quality Management Systems




