See the step by step complete solution below.
Explanation:
* Devices in both buildings should be able to access the Internet.
* Security insists that all Internet traffic be inspected before entering the network.
* Desktops should not see traffic destined for other devices.
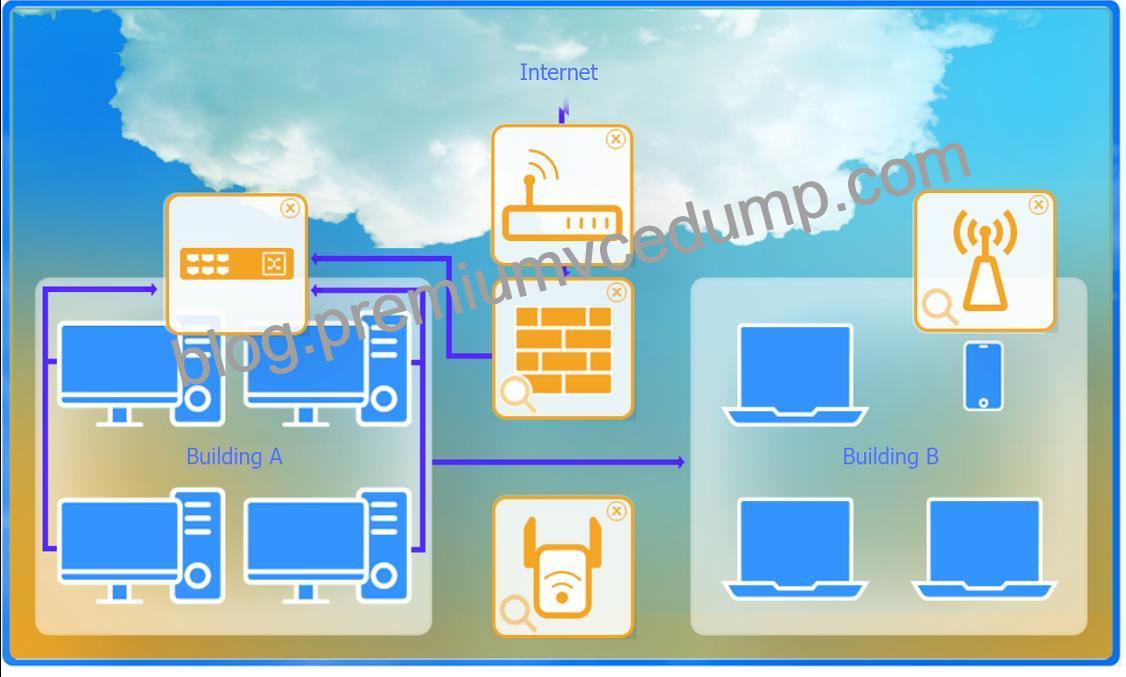
Here is the corrected layout with explanation:
* Building A:
* Switch: Correctly placed to connect all desktops.
* Firewall: Correctly placed to inspect all incoming and outgoing traffic.
* Building B:
* Switch: Not needed. Instead, place a Wireless Access Point (WAP) to provide wireless connectivity for laptops and mobile devices.
* Between Buildings:
* Wireless Range Extender: Correctly placed to provide connectivity between the buildings wirelessly.
* Connection to the Internet:
* Router: Correctly placed to connect to the Internet and route traffic between the buildings and the Internet.
* Firewall: The firewall should be placed between the router and the internal network to inspect all traffic before it enters the network.
Corrected Setup:
* Top-left (Building A): Switch
* Bottom-left (Building A): Firewall (inspect traffic before it enters the network)
* Top-middle (Internet connection): Router
* Bottom-middle (between buildings): Wireless Range Extender
* Top-right (Building B): Wireless Access Point (WAP)
In this corrected setup, the WAP in Building B will connect wirelessly to the Wireless Range Extender, which is connected to the Router. The Router is connected to the Firewall to ensure all traffic is inspected before it enters the network.
Configuration for Wireless Range Extender:
* SSID: CORP
* Security Settings: WPA2 or WPA2 – Enterprise
* Key or Passphrase: [Enter a strong passphrase]
* Mode: [Set based on your network plan]
* Channel: [Set based on your network plan]
* Speed: Auto
* Duplex: Auto
With these settings, both buildings will have secure access to the Internet, and all traffic will be inspected by the firewall before entering the network. Desktops and other devices will not see traffic intended for others, maintaining the required security and privacy.
To configure the wireless range extender for security, follow these steps:
* SSID (Service Set Identifier):
* Ensure the SSID is set to “CORP” as shown in the exhibit.
* Security Settings:
* WPA2 or WPA2 – Enterprise: Choose one of these options for stronger security.
WPA2-Enterprise provides more robust security with centralized authentication, which is ideal for a corporate environment.
* Key or Passphrase:
* If you select WPA2, enter a strong passphrase in the “Key or Passphrase” field.
* If you select WPA2 – Enterprise, you will need to configure additional settings for authentication servers, such as RADIUS, which is not shown in the exhibit.
* Wireless Mode and Channel:
* Set the appropriate mode and channel based on your network design and the environment to avoid interference. These settings are not specified in the exhibit, so set them according to your network plan.
* Wired Speed and Duplex:
* Set the speed to “Auto” unless you have specific requirements for 100 or 1000 Mbps.
* Set the duplex to “Auto” unless you need to specify half or full duplex based on your network equipment.
* Save Configuration:
* After making the necessary changes, click the “Save” button to apply the settings.
Here is how the configuration should look after adjustments:
* SSID: CORP
* Security Settings: WPA2 or WPA2 – Enterprise
* Key or Passphrase: [Enter a strong passphrase]
* Mode: [Set based on your network plan]
* Channel: [Set based on your network plan]
* Speed: Auto
* Duplex: Auto
Once these settings are configured, your wireless range extender will provide secure connectivity for devices in both buildings.
Firewall setting to to ensure complete compliance with the requirements and best security practices, consider the following adjustments and additions:
* DNS Rule: This rule allows DNS traffic from the internal network to any destination, which is fine.
* HTTPS Outbound: This rule allows HTTPS traffic from the internal network (assuming
192.169.0.1/24 is a typo and should be 192.168.0.1/24) to any destination, which is also good for secure web browsing.
* Management: This rule allows SSH access to the firewall for management purposes, which is necessary for administrative tasks.
* HTTPS Inbound: This rule denies inbound HTTPS traffic to the internal network, which is good unless you have a web server that needs to be accessible from the internet.
* HTTP Inbound: This rule denies inbound HTTP traffic to the internal network, which is correct for security purposes.
Suggested Additional Settings:
* Permit General Outbound Traffic: Allow general outbound traffic for web access, email, etc.
* Block All Other Traffic: Ensure that all other traffic is blocked to prevent unauthorized access.
Firewall Configuration Adjustments:
* Correct the Network Typo:
* Ensure that the subnet 192.169.0.1/24 is corrected to 192.168.0.1/24.
* Permit General Outbound Traffic:
* Rule Name: General Outbound
* Source: 192.168.0.1/24
* Destination: ANY
* Service: ANY
* Action: PERMIT
* Deny All Other Traffic:
* Rule Name: Block All
* Source: ANY
* Destination: ANY
* Service: ANY
* Action: DENY
Here is how your updated firewall settings should look:
Rule Name
Source
Destination
Service
Action
DNS Rule
192.168.0.1/24
ANY
DNS
PERMIT
HTTPS Outbound
192.168.0.1/24
ANY
HTTPS
PERMIT
Management
ANY
192.168.0.1/24
SSH
PERMIT
HTTPS Inbound
ANY
192.168.0.1/24
HTTPS
DENY
HTTP Inbound
ANY
192.168.0.1/24
HTTP
DENY
General Outbound
192.168.0.1/24
ANY
ANY
PERMIT
Block All
ANY
ANY
ANY
DENY
These settings ensure that:
* Internal devices can access DNS and HTTPS services externally.
* Management access via SSH is permitted.
* Inbound HTTP and HTTPS traffic is denied unless otherwise specified.
* General outbound traffic is allowed.
* All other traffic is blocked by default, ensuring a secure environment.
Make sure to save the settings after making these adjustments.
